Wazuh was created in 2015 as a SIEM (Security Information and Event Management) platform and offers functions for detecting and responding to cyberthreats and controlling the status of systems that it covers. It is a free-of-charge tool based on the OSSEC (Open Source HIDS SECurity) system, which is a popular platform for detecting intruders in computer systems. The Wazuh system environment consists of three main components:
- Wazuh indexer is responsible for searching, storing and indexing data;
- Wazuh manager acts as the main module that collects and analyzes the received data;
- Wazuh dashboard constitutes the user interface.
Extensive capabilities
The platform is a HIDS (Host-Based Intrusion Detection System) tool, and therefore its primary way of collecting information is by obtaining it from systems via agents installed on them. These agents collect data on configuration, installed programs and modules, as well as other events.
The application has a function for managing groups. Using them, we are able to centrally and collectively manage the configuration of agents on multiple machines at the same time, which means greater efficiency and consistency of settings.
The options of integration with other tools make it easy to expand Wazuh’s capabilities. An example is interoperation with Suricata (to analyze network traffic) or Virustotal (file inspection for infection).
The resulting XDR (Extended Detection and Response) Wazuh tool is able to protect devices based on different systems (including Windows, Linux, MacOS or AIX).
The system in question is an open source tool, meaning that its code is publicly available. This allows users to check its features and configurations, which provides more control over the protection of their IT systems. In addition, the Wazuh community is active and supports the development of the tool by providing updates, patches and new features. The system continues to be developed and its documentation significantly facilitates the implementation process.
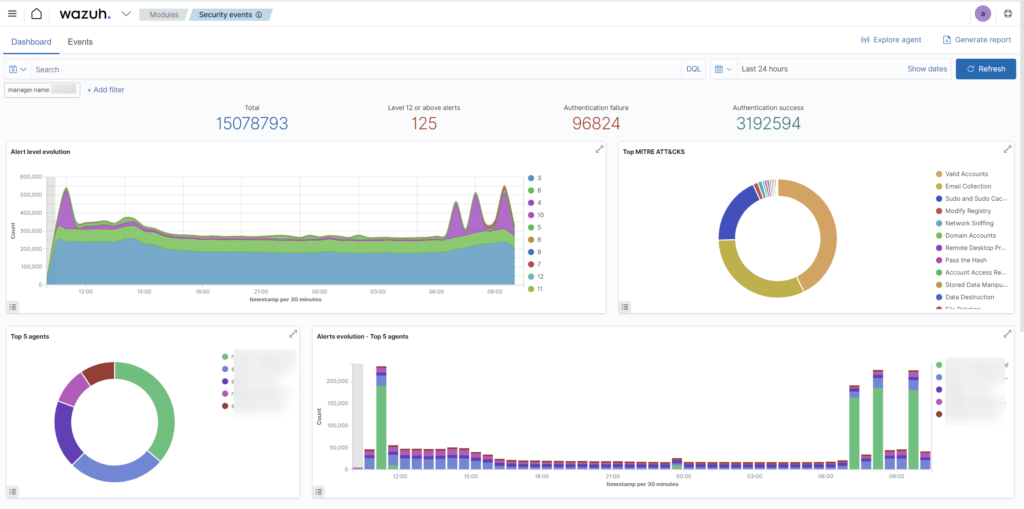
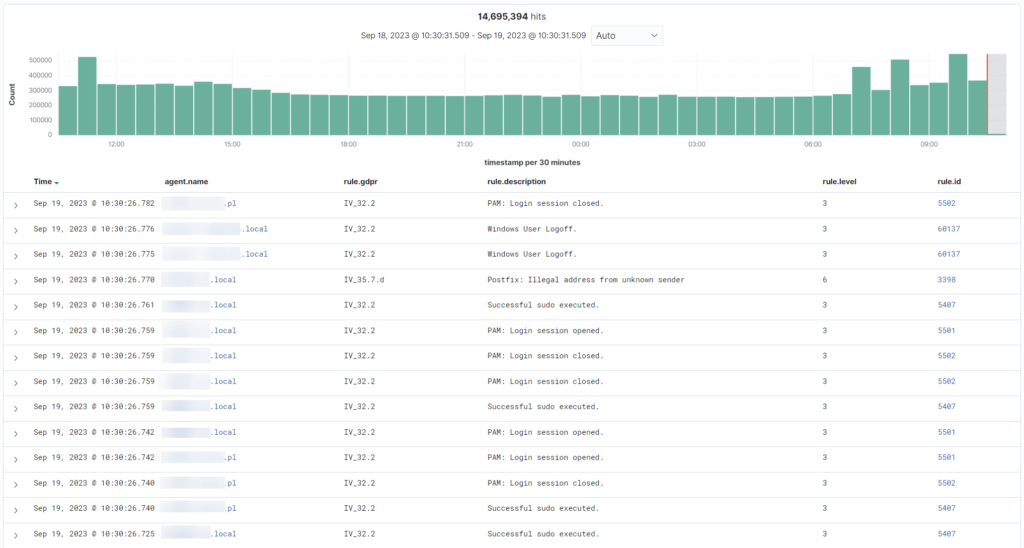
The capabilities of the tool are extensive. It collects and analyzes data from system logs in real time. After analyzing the information and comparing it with the rule database, it presents the results and, if necessary, sends alarms via e-mail or SMS (integration with AWS SNS). Examples of such notifications include successful/unsuccessful escalation of user privileges, an application error or use of all memory on the monitored system. Wazuh has over 4,000 default rules defined in its database that respond to events. In addition, the user can edit and write their own rules.
All of Wazuha’s capabilities are linked to MITRE ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) functionality. This involves correlating the events recorded by the tool with known techniques used by attackers. An example may be a multiple login attempt (a suspected password guessing attack) or unauthorized access to files using the directory traversal method. Thus, Wazuh makes it easy to spot a dangerous situation in a large number of logged incidents and to trigger an automatic response.
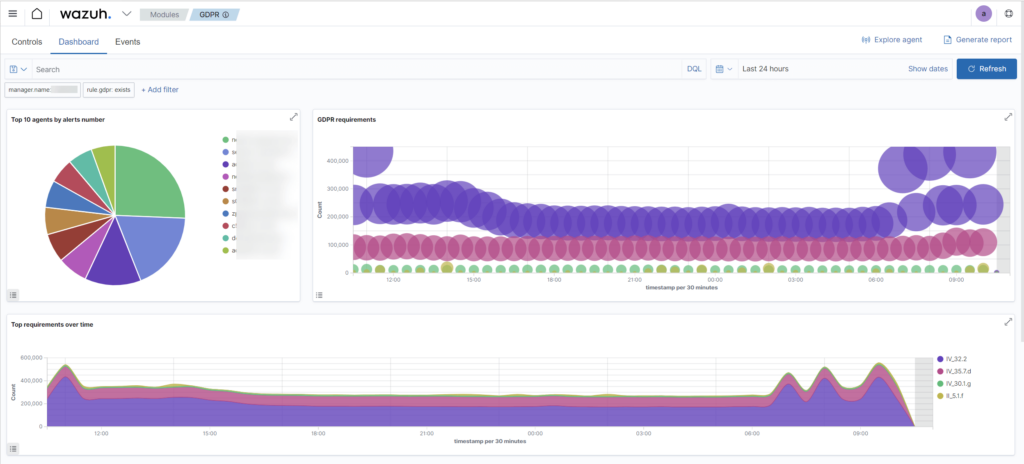
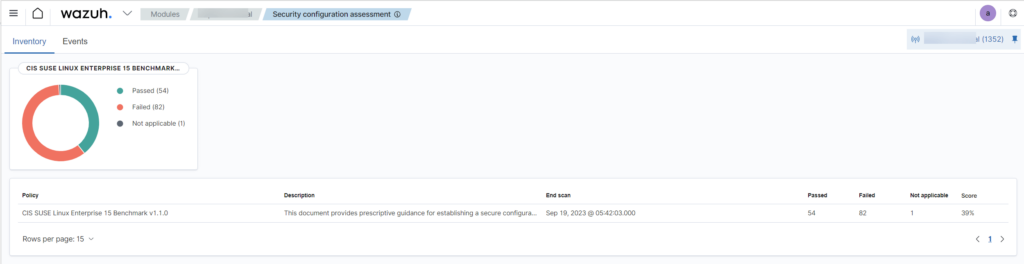
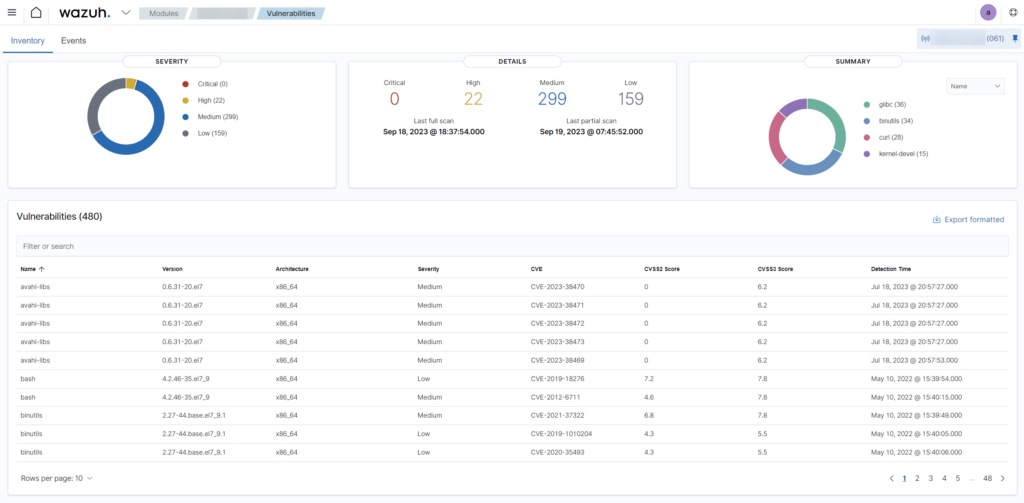
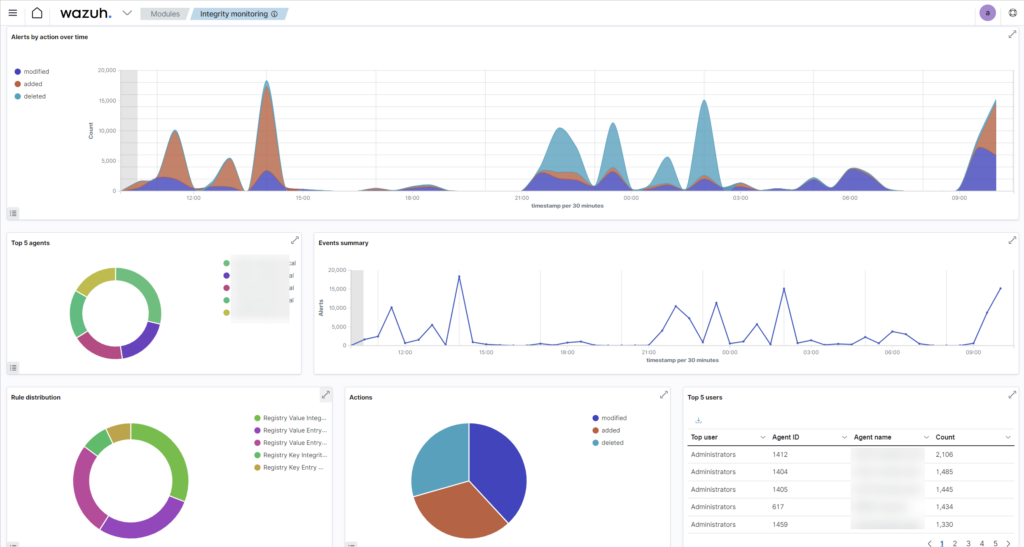
Wazuh – sample dashboards
Responding effectively to incidents
The problem faced by security teams is an effective response to incidents. When an incident occurs, it must first be detected, then analyzed, and only in the next step can it be adequately responded to. Unfortunately, this is a time-consuming process, which in practice makes it impossible to effectively react manually to incidents in real time.
Wazuh also comes to the rescue here, as it has the function of actively responding to threats. This option allows you to use ready-made scripts that enable automatic blocking of the user or the IP address of the attack source, among other things. In addition to ready-made scripts, the system allows you to program your own scripts and completely adapt them to your needs. With this feature, it is possible to virtually block an attack when it occurs.
In order to break into systems, criminals exploit existing vulnerabilities, that is, gaps in operating systems or installed applications. The basic countermeasure is to make timely updates that will eliminate these vulnerabilities. Wazuh will also help you in this matter, since its primary function is to monitor the system for vulnerabilities.
The knowledge base for Wazuha is the National Vulnerability Database (NVD) and operating system providers. Wazuh informs the user about the level of threat, the unique CVE identifier, the name of the application affected by the vulnerability, the current version of the application and the recommended version that patches the indicated vulnerability.
The system also scans selected files for their integrity (FIM, File Integrity Monitoring). For this purpose, metadata including file size changes, file access permissions, content changes, and MD5, SHA1, and SHA256 checksums are analyzed.
This product also enables analysis of compliance with regulations and standards. The tool analyzes system settings and available logs for compliance with security requirements. Currently, Wazuh supports such standards as: PCI DSS, RODO, NIST 800-53, GPG13, TSC SOC2 and HIPAA.
Wazuh is a comprehensive tool for monitoring, detecting and responding to cyberthreats, offering advanced event detection, security management and integration with other tools. As a free and open source solution, it can be an attractive choice for organizations looking for an effective and low-cost tool that will protect them against cyberattacks and help meet regulatory requirements related to data security.
However, the tool requires proper configuration and management to be fully effective in protecting against cyberthreats. Wazuh implementation may require advanced IT security knowledge and experience in configuring and managing security tools. All for One Poland’s consultants are here to help.

Waldemar Sokołowski, Board Member, IT Services Director, All for One Poland
Pillars of cybersecurity
For any organization, the need to protect its own human, financial or legal resources is obvious. However, in the case of information resources – security is often insufficient, despite the fact that it is information that determines the competitive advantage and market position of many companies. The reasons for this are varied – from the lack of proper assessment of the value of data, through an unawareness of the consequences of incidents, to a deficit of competencies in the area of cybersecurity.
Effective information protection must be based on identifying key information assets and the risks that affect them. Importantly – this task may not be the sole responsibility of IT. It needs the support and involvement of top management. This approach enables the selection of optimal solutions – organizational and technical, as well as the rationalization of the budget allocated to cybersecurity. The results for the organization are both management regulations – allowing the use, measurement and improvement of the effectiveness of protection, and technical solutions – which translate directly into ensuring confidentiality, integrity and availability of information resources.
As far as technical solutions, are concerned, one of the pillars of cybersecurity is SIEM tools, designed for analytics and visualization of events in IT/OT systems. Their basic functionalities include centralization of logs from the entire environment (IT devices, applications, databases, industrial automation and other), processing and reporting. A comprehensively implemented SIEM system is both an operational tool for administrators and a primary source of information on the state of IT security for the CIO/CISO.
All cybersecurity incidents leave traces in systems. If the incident is a cyberattack, its symptoms can most often be observed in advance, identifying anomalies in network traffic, redundant authentication attempts, vulnerabilities in IT systems, etc. The added value of using SIEM systems results from such a form of correlating and presenting data that will enable the organization to quickly take actions appropriate to the situation.
Waldemar Sokołowski, Board Member, IT Services Director, All for One Poland