NIS2: From Compliance to Resilience
Prepare Your Company for Crises
The NIS2 directive and the National Cybersecurity System Act mark a turning point: from "we have a security policy" to real operational resilience – with clear management accountability, efficient IT, a committed quality department, and secured production (OT). Proper implementation of NIS2 is not just about meeting regulatory requirements. A well-built and applied cybersecurity management system reduces the risk of attack, shortens downtime, and limits the impact of crises. Don't wait for the law. Start implementation today.
The NIS2 directive and the National Cybersecurity System Act mark a turning point: from "we have a security policy" to real operational resilience – with clear management accountability, efficient IT, a committed quality department, and secured production (OT). Proper implementation of NIS2 is not just about meeting regulatory requirements. A well-built and applied cybersecurity management system reduces the risk of attack, shortens downtime, and limits the impact of crises. Don't wait for the law. Start implementation today.
NIS2 – A New Dimension of Organizational Resilience
The NIS2 Directive (Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity) is a new version of the NIS Directive. It aims to increase the level of cybersecurity in the European Union – especially among companies that were not covered by the first version of the directive. NIS2 introduces new responsibilities for Member States and expands the scope of entities covered by obligations to effectively secure data and information.
In Poland, it will be implemented through an amendment to the Act on the National Cybersecurity System (KSC), which is currently awaiting adoption (legislative work is underway). The aim of the regulation is not only to protect IT/OT networks and systems, but to increase the overall resilience of an organization – understood as business continuity and the ability to deliver goods and services throughout the supply chain without interruption, including in crisis situations such as a natural disasters, targeted attacks on IT systems or sabotage.
In addition to typical technological risks, NIS2 also refers to environmental risks, supply chain disruptions, and unforeseen that can bring a company’s operations to a halt.
Who the New Regulations Will Cover
Obligations under NIS2 will apply to two groups of entities: essential and important.
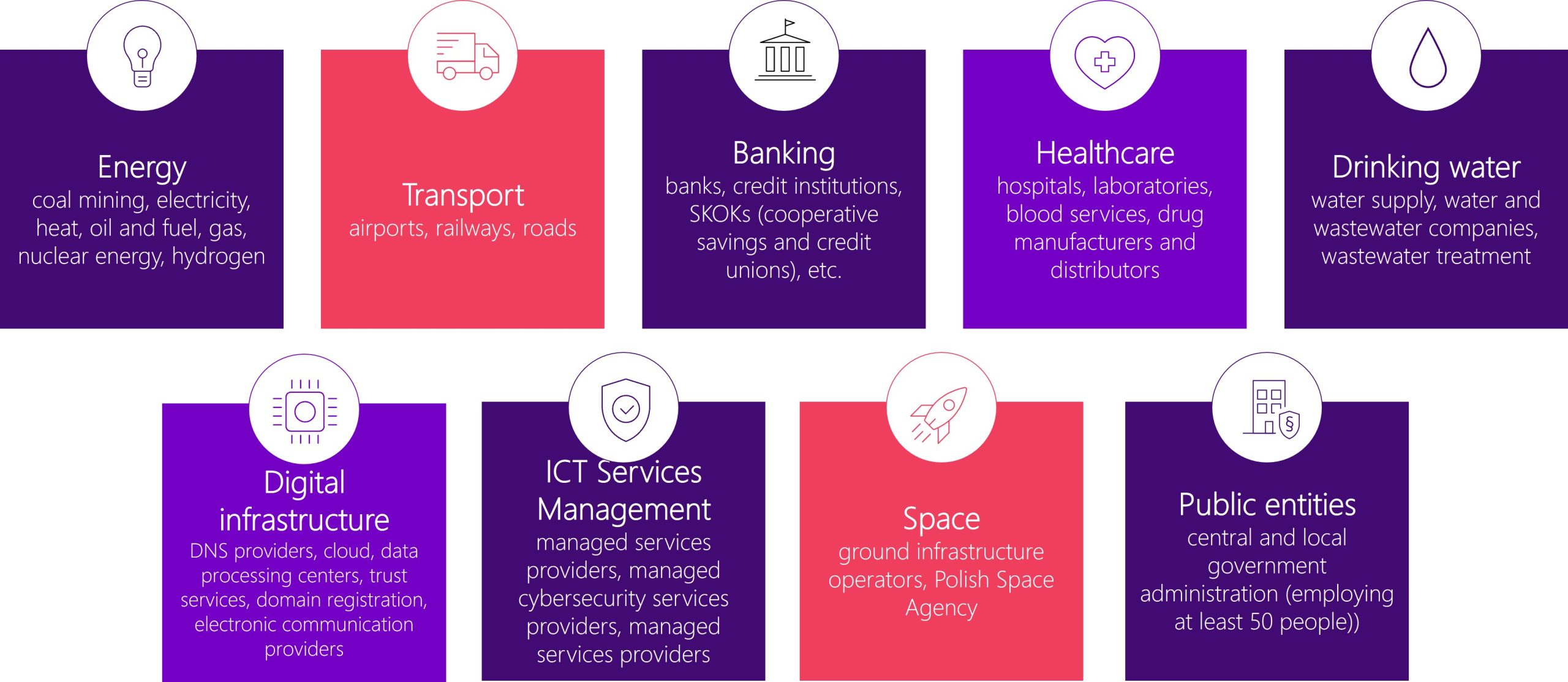
Essential entities are those whose activities (not only their core activities) are considered critical to the functioning of the state, including entities in the energy sector, transport, banking, healthcare, drinking water supply, digital service provision, and public administration, among others.
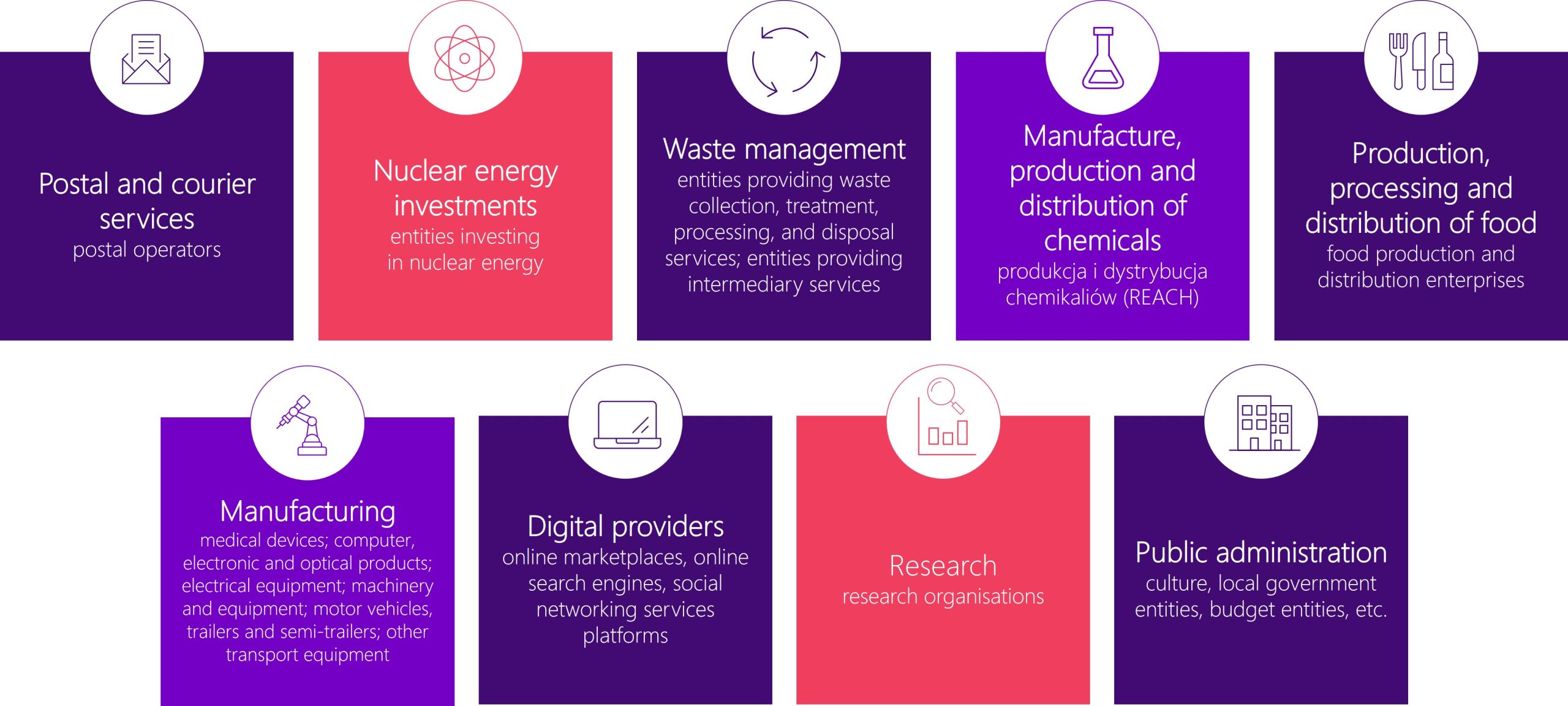
Important entities included companies in important sectors, such as postal services, waste management, manufacturing and distribution, chemicals, food production, and industrial manufacturing (e.g., automotive).
Manufacturing companies must fall under these requirements, as their operations are crucial to the functioning of the state, both economically and in terms of the ability to produce specific vehicles, equipment, or components.
Despite the distinction between essential and important players, the scope of requirements and tasks for both groups will be in practice very similar (minor flexibilities for important entities concern proportionality or a lower version of safeguards).
The basic requirements are:
- Implementation of an Information Security Management System, which will cover all key aspects of security, such as:
- Asset inventory (including in production environments)
- Risk analysis and decisions on risk treatment
- Ensuring IT security (e.g., appointing cybersecurity officers, infrastructure hardening, threat detection, change control, vulnerability management, defining emergency and backup procedures)
- Providing employee training and awareness programs
- Analysing and implementing physical security measures (e.g., access control, door reinforcement, secured turnstiles, entry and exit control, perimeter fencing, etc.)
- Implementation of a Business Continuity Management System, which will complement information security with operational business continuity aspects (e.g., relocation to an alternative site, detailed procedures for all company departments, testing of action plans and staff response training)
- Designation of contact persons within the national cybersecurity system;
- Training of top management at least once a year;
- Regular internal and external audits;
- Reporting incidents to state authorities.
In practice, an organization should implement a well-functioning set of both organizational (policies, procedures, instructions), technical (cybersecurity, IT/OT threat detection and business continuity solutions) and competency (e.g., training) solutions.
Essential Sectors under NIS2
Deadlines and Obligations
Although the effective date of the Act on the National Cybersecurity System has not yet been confirmed, the draft amendment outlines a timetable of actions for companies covered by the new regulations. Once the Act is published, companies will have:
- 3 months to conduct a self-assessment against the KSC criteria and register as essential or important entities,
- 6 months (after registration) to comply with the requirements – primarily by implementing an Information Security Management System (ISMS) with business continuity elements,
- 2 years to carry out an independent audit confirming the effectiveness of implemented security measures and compliance with NIS2 regulations.
Important Sectors under NIS2
Does the Company Fall Under NIS2?
It is known that NIS2 will apply to large or medium-sized companies. In such companies, in order to verify whether the company will be subject to the obligation to implement the requirements of the regulation, an analysis should be carried out to assess whether specified criteria are met.
Subsequently, other areas of the company’s business should be reviewed, because even if only one of them (a less important, ancillary aspect) falls under NIS2, the whole enterprise may be considered essential or important. For example, if a company is engaged in manufacturing, but also provides transportation services, this area of business should be analyzed.
If the analysis shows that the company falls within the scope of NIS2 obligations, it should register in the National Register of Essential and Important Entities.
It is worth noting that in the event of a change or expansion of the scope of the company’s activities, the analysis must be repeated and – if necessary – the company must register accordingly. Failure to fulfil this obligation and to comply with NIS2 requirements may result in severe financial penalties.
Neither ISO27001 (ISMS) certification, ISO 22301 (business continuity) nor any industry certification (e.g., TISAX, TPN) exempts a company from implementing KSC (NIS2) requirements. The good news, however, is that companies with ISO 27001 certification have already completed a large portion of the required tasks.
Four Perspectives of NIS2 in the Organization
Concern for information security, physical security, and business continuity is a joint effort across the entire organization. However, the majority of tasks and responsibility lie with management, the IT department, the quality department, and the production area, where OT security plays an important role alongside IT systems.
We present these four perspectives of NIS2 in the organization.
Management – Responsibility and Awareness
According to the draft Act, top management (the head of the entity) is personally responsible for ensuring cybersecurity. This means an obligation to actively engage in the security management process, participate in risk analysis, and make decisions on the implementation of security safeguards.
At least once a year, the head of the entity will be required to complete training on NIS2 requirements, and their involvement will become one of the elements of the audit. Importantly, it is collaboration between management and IT and quality teams that can facilitate the justification of security budgets and investment decisions.
Building awareness among management of the risks associated with business continuity, and the consequences of its disruption for the company’s key processes and resources is an essential element of an effective and well-funded security system.
IT – The Heart of Cyber Resilience
An organization’s cybersecurity is influenced by all departments and employees, but it is the IT department that plays a key role in ensuring the highest possible standards and operational practices.
The IT department will be responsible for fulfilling technical requirements, including:
- Implementation and maintenance of an Information Security Management System
- Incident management and reporting to the relevant authorities
- Providing continuous monitoring of systems security (SOC – Security Operations Center).
For IT, implementing the solutions required by NIS2 can be an opportunity to organize documentation and processes, and to obtain formal management support in areas that have so far often been postponed, such as documenting procedures, asset inventory, or risk analysis. It is also a good opportunity to raise business awareness of IT capabilities (e.g., the time required to restore a system) and, conversely, for IT to learn about business needs (how much data loss is acceptable and what costs it entails).
It should also be kept in mind that the new information security obligations (such as system monitoring, reviews, and the need to provide documented procedures and instructions) will require a certain level of effort, which may mean the need to ensure appropriate resources (personnel or equipment).
Quality – Integration of Management Systems
The Information Security Management System naturally combines with the quality approach – the PDCA (plan-do-check-act) cycle. Therefore, the quality department should be actively involved in building the system. In large, mature organizations, quality department staff often have competencies that can facilitate demonstrating accountability, such as knowledge of auditing principles, process modelling, employee awareness management, and familiarity with the Deming cycle.
Integrating systemic cybersecurity management with existing quality management systems can significantly simplify the management of documentation, audits and improvement processes.
Manufacturing – OT Security and Business Continuity
In industrial environments, security does not end with IT. Automation systems (OT) are increasingly becoming targets of cyberattacks, and their downtime can paralyse an entire plant.
The foundation for preparing to implement NIS2 requirements is an inventory of production assets and risk analysis in the OT environment, as well as the development of business continuity plans and incident response scenarios.
It is worth remembering that production disruption can occur for many reasons, not only cybersecurity-related ones. Physical security matters, including access control, employee training, and securing the work area, are also covered by the KSC.
Building a Security System Step by Step
Building an NIS2-compliant cybersecurity management system involves four main steps:
- Asset and process identification – mapping information and technology assets.
- Risk analysis – identifying threats, vulnerabilities and impacts of potential incidents.
- Implementation of security measures – technical, organizational and procedural.
- Verification and improvement – regular audits, tests and procedure updates.